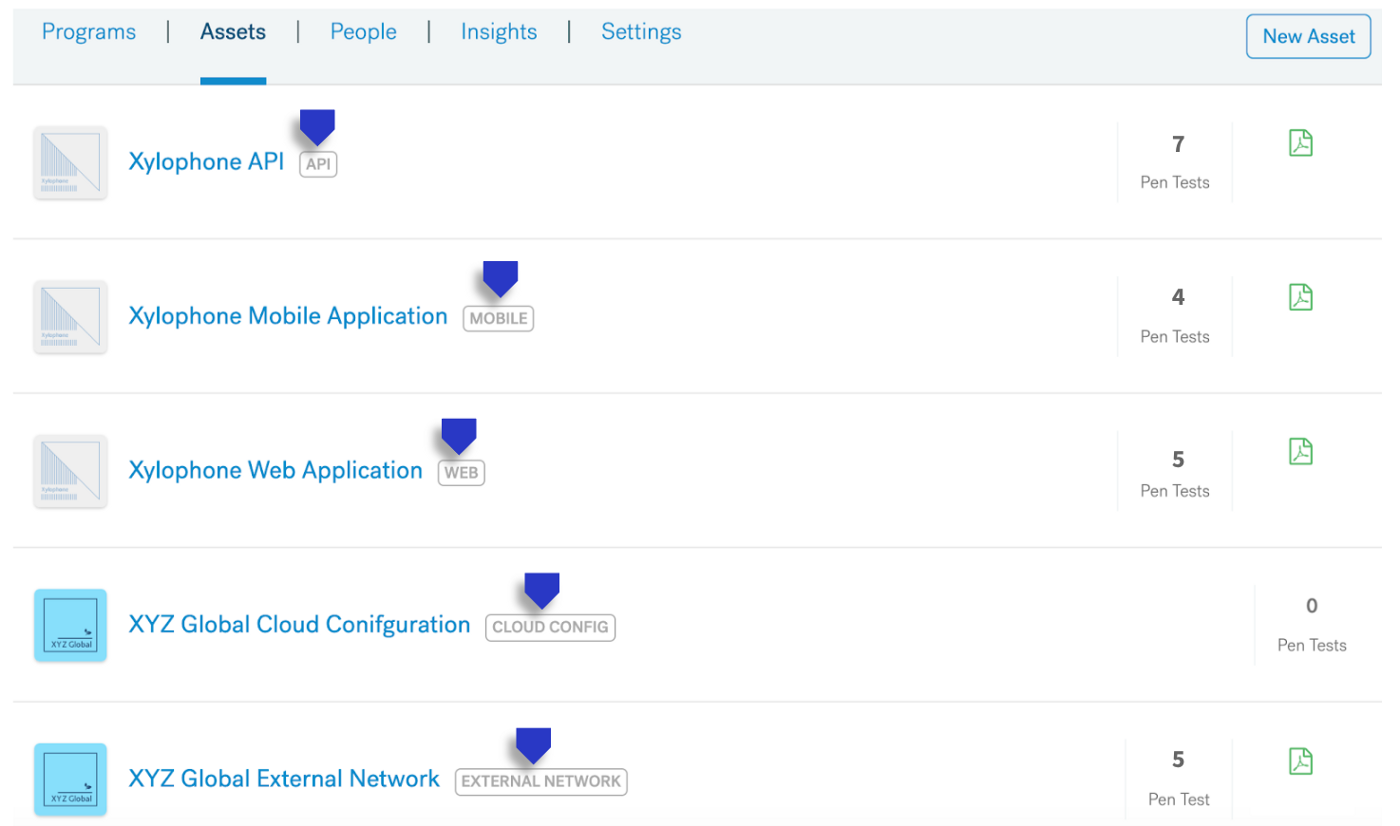
We are excited to introduce — Assets.
In Cobalt terminology, an Asset is the highest level under which you can group your testing efforts by their scope — such as a Web Application, a Mobile App, an API, an External or Internal network, or a Cloud instance.
Here are the benefits you can start taking advantage of once your pentests are grouped under assets:
- Improved management and efficiency for consecutive rounds of pentesting
An asset allows you to group all the important documentation and collateral that pentesters will need; including user model overviews, API documents, and video walk-throughs. Before starting a new pentest, you can easily review the asset to ensure all this information is up to date, ensuring new teams have a complete overview. There’s no need to submit the same information over again.
- Ease in tracking your pentesting progress
You can easily see and track the progress of each pentest for an asset all on one page. This is especially helpful when you need to do multiple rounds of pentesting concurrently and need to easily see how many vulnerabilities were found.
- Improved quality of time spent on pentesting
We know it’s not always possible for security and development teams to have all the vulnerability findings fixed before the next round of pentesting. By grouping all your pentests under an asset, you can now easily see which findings should be carried over to the next round of pentesting. Assets also provide valuable information to the researcher team on what vulnerabilities were previously found. This ensures that all relevant findings are consolidated on the latest pentest.
And last, but not least, Assets will enable you to take advantage of another new feature — Cobalt Insights! With Insights, you can now track and compare your pentest findings by criticality, status, and* the type* — helping you effectively act upon the most critical vulnerabilities by knowing where you need to prioritize your remediation efforts.

Track and compare your pentest findings by criticality, status, and the type